Signing git commits

Why would I want to sign my git commits?
Quite simply put, it is to add confidence in the commit change comes from the contributor it says it does!
This would be more appropriate for open source projects where anyone and everyone can contribute, but there is no harm in falling into a nice workflow with a good practice of working safely and proving origin.
Ok, I'm sold. How do i set this up?
I'm not going to walk through all the steps or why they exist because there are so many great resources out there that document this simple process.
I will link this resource which is part of the GitHub documentation and probably the place to start.
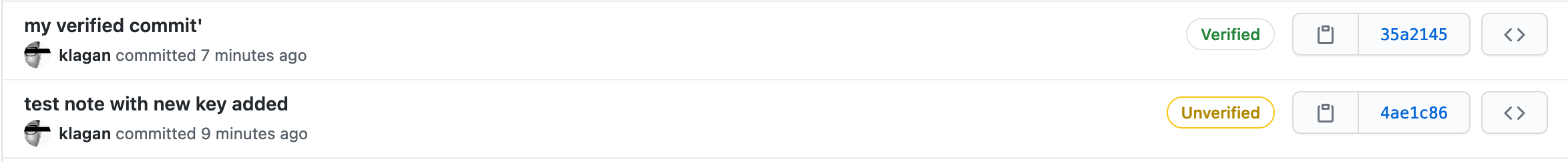
Checking existing GPG keys
extracted from link above
Use the gpg --list-secret-keys --keyid-format=long command to list the long form of the GPG keys for which you have both a public and private key.
A private key is required for signing commits or tags.
$ gpg --list-secret-keys --keyid-format=long
Note: Some GPG installations on Linux may require you to use gpg2 --list-keys --keyid-format LONG to view a list of your existing keys instead. In this case you will also need to configure Git to use gpg2 by running git config --global gpg.program gpg2.
From the list of GPG keys, copy the long form of the GPG key ID you'd like to use.
In this example, the GPG key ID is 3AA5C34371567BD2:
$ gpg --list-secret-keys --keyid-format=long
/Users/hubot/.gnupg/secring.gpg
------------------------------------
sec 4096R/3AA5C34371567BD2 2016-03-10 [expires: 2017-03-10]
uid Hubot
ssb 4096R/42B317FD4BA89E7A 2016-03-10
I have multiple git accounts for different things. How do I manage this?
To resolve this we need to segregate our local repositories.
In this example I will illustrate how to set up my work account and my personal account.
- Create a folder for your
workrepositories and a folder for yourpersonalrepositories.
mkdir ~/source/work
mkdir ~/source/personal
2. Edit your ~/.gitconfig to configure the fact that we have two git accounts and they have separate configuration locations:
[includeIf "gitdir:~/source/work/"]
path = ~/.gitconfig-work
[includeIf "gitdir:~/source/personal/"]
path = ~/.gitconfig-personal
3. Create the git configuration files for each git account
For my work account, I may have a simple configuration like this:
[user]
name = Kuku Frango
email = kuku@work.com
For my personal account, I may have a more advanced configuration that includes automatically signing my commits like this:
[user]
name = Kuku Frango
email = kuku@personal.com
signingkey=ABC1DE23FGHIJ45K
[commit]
gpgsign=true
That should be all you need to get started. For more advanced git configuration you can read about options here.
Troubleshooting
git fatal: No credential backing store has been selected
After having installed the git credential manager core, you may be presented with the above error message when attempting to clone a repository.
This can be remedied by running the following command:
git config --global credential.credentialStore secretservice
